In a normal IP communication between two hosts, the sending host inserts its configured IP address in the ‘source IP’ field of the IP header, in order for the receiving host to know where to send the reply traffic back. In IP Spoofing, a malicious host can forge the IP header and change the source IP address to something different, thus making the packet to appear that it’s coming from a different machine.
IP spoofing is frequently used in Denial of Service attacks, where the attacker wants to hide its identity (source IP address) and also does not care about receiving responses to its attack packets.
One of the most effective ways to defend against IP spoofing is by proper packet filtering on your Gateway Router. This Router can perform ingress filtering on inbound traffic, and egress filtering on outbound traffic. Specifically, ingress filtering blocks packets from outside the network that have source addresses that belong to the inside network. Egress filtering blocks packets from inside the network that have source addresses that do not belong to the inside subnet.
An example network is shown below:
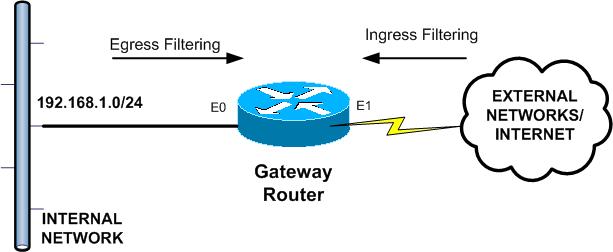
In our example above, our Gateway Router is a Cisco router connecting our Internal Network (with subnet 192.168.1.0 / 24) with other External Networks or even the Internet. To protect from IP spoofing, we should apply Ingress Filtering on the Outside Interface E1, and Egress Filtering on the Inside Interface E0. The configuration commands are shown below:
Ingress Filtering
In Ingress Filtering, we drop packets with source address 192.168.1.0 coming from Outside into our Network.
Router(config)# ip access-list extended INGRESS
deny ip 192.168.1.0 0.0.0.255 any
Router(config)# interface E1
Router(config-if)# ip access-group INGRESS in
Egress Filtering
In Egress Filtering, we check the source address of the Outbound Traffic, so that we allow only source addresses in the range 192.168.1.0/24 and drop everything else. This means that a potential malicious host inside our own network, can not change its source address to perform IP Spoofing attacks to External Networks.
Router(config)# ip access-list extended EGRESS
permit ip 192.168.1.0 0.0.0.255 any
deny ip any any
Router(config)# interface E0
Router(config-if)# ip access-group EGRESS in
Leave a Reply